Views

In the competitive industrial manufacturing landscape, where efficient operations can determine success or failure, optimised alarm configurations are critical. A company’s reputation is often measured by its environmental impact and operational efficiency. Implementing effective alarm configurations ensures facilities operate efficiently and cost-effectively, helping businesses stay ahead.
However, deviations from approved alarm configurations can have significant reputational and financial consequences. Unauthorised changes can increase operating costs, impact maintenance and safety, and disrupt operations. What may seem like a minor adjustment can trigger a cascade of inefficiencies, resulting in financial and operational nightmares.
Imagine a seemingly minor adjustment to an industrial control system, such as a small change in a production line’s temperature setting or the unapproved modification of a motor’s speed. Initially, everything appears normal. But over time, energy consumption rises, equipment underperforms, and production efficiency declines. In worst-case scenarios, these inefficiencies may lead to operational disruptions.
Beyond energy costs, inefficient configurations result in suboptimal performance. Machines running outside their ideal parameters experience accelerated wear and tear, leading to increased maintenance expenses and reduced lifespan. In some cases, improper configurations cause frequent breakdowns, forcing companies to allocate substantial budgets for repairs and replacements.
Product quality is another key concern. Incorrect system configurations can cause defects, leading to costly rework or wasted materials. For example, an incorrect pressure setting on a production line could result in defective products, increasing material waste and operational downtime.
Unauthorised changes are not always internal actions. Cybersecurity threats are a growing concern, as malicious actors can introduce inefficiencies to disrupt operations. Attackers gaining unauthorised access to control systems may manipulate configurations, making tracing disruptions challenging. This highlights the need for secure control systems to prevent both intentional breaches and unintended misconfigurations.

Given the potential impact of unauthorised changes, it is no surprise that alarm management standards emphasise their importance. The ISA-18.2 standard, for instance, considers the number of unauthorised alarm configuration changes as a key metric for assessing alarm management commitment. Without proper monitoring, identifying and investigating these changes becomes impossible.
To prevent costly inefficiencies, robust access controls must be in place. Every control system change should be logged and authorised by appropriate personnel. In my experience many SCADA and DCS systems lack detailed audit trails for MOC, providing only basic details like who made a change. The absence of contextual information often necessitates cumbersome manual documentation processes, delaying approval and implementation.
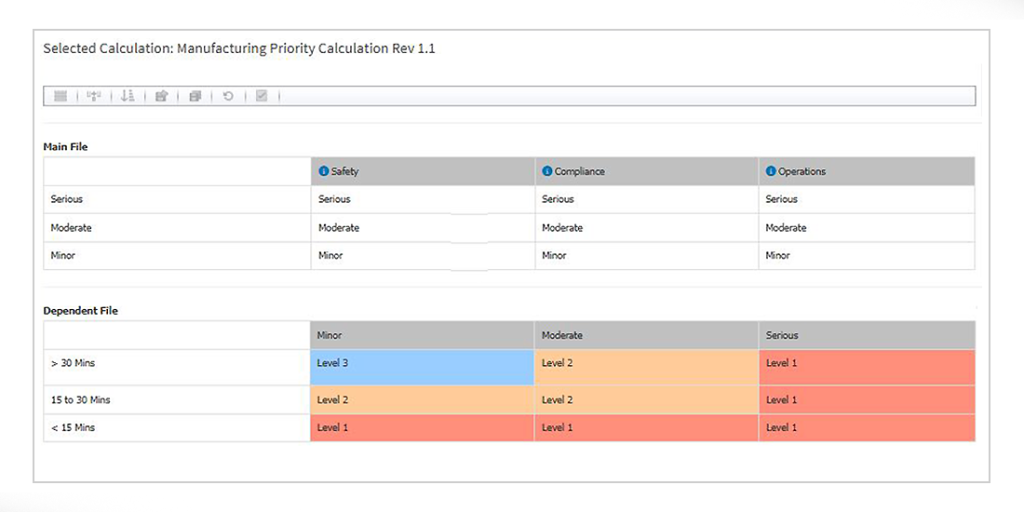
However, these traditional approaches fall short in identifying unauthorised changes, making it difficult to take corrective action. This is where a Master Alarm Database like ProcessVue Guardian can significantly improve change management procedures.
ProcessVue Guardian serves as the central repository for alarm configurations, enabling structured and secure change management through several key features:
-
Comparison Between MADb and Live Systems
Once alarm configurations are imported into ProcessVue Guardian, rationalised, and deployed, a comparison can be performed between the MADb and the live system. By exporting the running alarm configuration and re-importing it into Guardian, users can highlight unauthorised changes and investigate them. If necessary, these changes can be rolled back, preventing unnecessary wear and tear on operations.
-
Approval Workflow for Controlled Changes
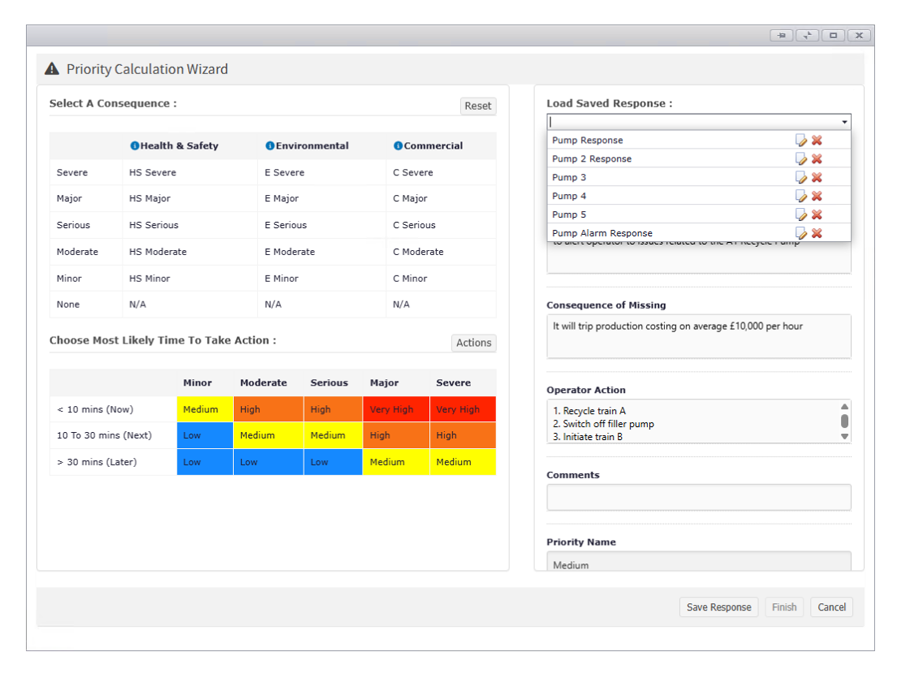
An approval workflow ensures that alarm configuration changes undergo review and authorisation before deployment. Changes must be assessed and approved by designated personnel. Only approved changes can be implemented, ensuring that all modifications are considered before application.
-
Projects for Structured Alarm Management
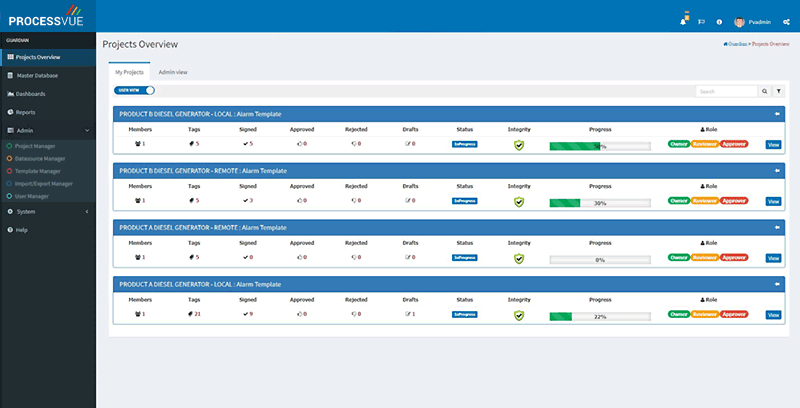
ProcessVue Guardian utilises projects to structure alarm rationalisation and documentation activities. Projects allow segmentation of alarms and restrict access to authorised personnel, ensuring only designated users can modify configurations. This enhances security and accountability in alarm management.
-
Comprehensive Audit Trails
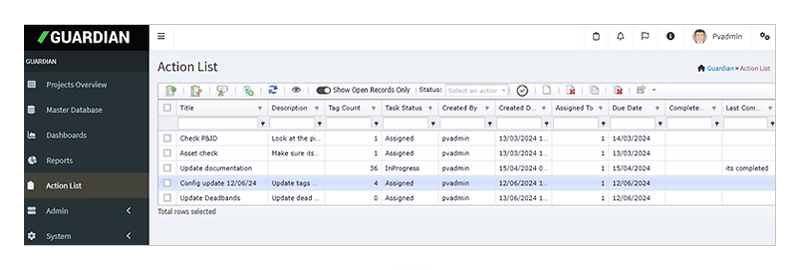
Every alarm configuration change is automatically recorded, detailing who made the change, what was modified, and when the change occurred. This full audit trail simplifies compliance reviews and enhances transparency in MOC practices.
-
Version Control for Tracking Changes
ProcessVue Guardian employs a robust version control system, applying both minor and major version numbers to alarm configurations. Minor versions track iterative changes, while major versions indicate full deployments. This systematic tracking enables users to monitor and manage configuration history effectively.
Industrial engineers play a crucial role in optimising systems to maximise efficiency and minimise costs. Inefficient configurations pose a silent yet significant threat, potentially leading to severe financial and operational consequences. By leveraging a Master Alarm Database like ProcessVue Guardian, organisations can enhance their management of change governance, promptly identify unauthorised modifications, and protect their operations, bottom line, and environmental impact.
With ProcessVue Guardian, facilities can ensure a structured, secure, and efficient approach to alarm management, enabling them to stay ahead in an increasingly competitive industrial landscape.